Here are few hacks to use with Google Talk:
1. Did you ever wish to run two instances for GTalk? This is possible and plain simple. Navigate to the shortcut that launches Google Talk (if not available, right click on C:\Program Files\Google\Google Talk\googletalk.exe and select Create Shortcut). Open properties. Add /nomutex in the target textbox.
2. To keep GoogleTalk always on top: Go to the registry entry HKEY_CURRENT_USER\Software\Google\Google Talk\Options, create a new DWORD show_pin and set its value to 1. Restart GTalk and you will see a pin near the minimize button.
3. To bring all GTalk windows in front press [Win] + [Esc] keys on keyboard.
4. To write in bold use *this text is bold* and for italic _this is italic_.
5. Coping someone’s avatar: Navigate to %userprofile%\AppData\Local\Google\google talk\avatars\. This directory contains all avatars cached in PNG format (rename them). Search by email in avatar.txt to find your friends avata
Tuesday, December 30, 2008
Monday, December 15, 2008
TopTricks for Windows Xp
Disabling Scandisk
When Windows is not shut down correctly, it will perform an AutoCheck
using CHKDSK on the next restart.
AutoCheck is executed after a short time delay. AutoCheck can be
disabled or delayed by tweaking a few Registry settings.
Run ‘Regedit’ from ‘Start Menu|Run...’
Go to ‘HKEY_LOCAL_MACHINE|SYSTE
M|CurrentControlSet|Control|Session
Manager’.
Create a new DWORD value, or
modify the existing value, called
“AutoChkTimeOut” and set it according
to the value data below.
Value Name: AutoChkTimeOut.
Data Type: REG_DWORD (DWORD Value).
Value Data: Time in Seconds or 0 to disable
(default = 10).
Exit your registry, you may need to
restart or log out of Windows for the
change to take effect.
Monitoring the system
There are various applications you can use to monitor the state of your
system at any given time. One of them is a program called CoolMon (www.coolmon.org) where you can monitor about 22 of
the most geekiest system parameters like the temperature and speed of your system fans, the number of processes running, the total available memory on your hard disk and RAM, CPU utilization, etc. Each
of these can be individually con. gured to appear on the interface. Best of all, this monitoring happens in real time. Better still, the program is free.
If you need more details than what is offered by Windows System Information or the Device Manager, try out an application called Everest Home Edition (www.lavalys.com). This application hunts through your hardware and software setup and extracts every piece of information you might need about your processor, motherboard, graphics card,
hard disk and any other piece of hardware or software information that you might care to know about your computer.
Compress drive to save disk space
its not possible to increase ur memory size but u can compress ur data to save ur disk space, this feature is available in NTFS drive..
if u have a fat or fat32 drive, u can convert it to ntfs by running a command on dos:
for c drive:
convert c:/fs:ntfs
for d drive:
convert d:/fs:ntfs
for e drive:
convert e:/fs:ntfs
run the command similarly if u have more drive...
Compresing data in NTFS
* open my computer
* select any drive(drive with NTFS format)
* right click and select properties
* click on general tab
* select "compress drive to save disk space"
* Apply and OK
ur data will remain safe...
- Changing the Location of Special Folders
You can modify the registry to change the location of special folders like:
* My Documents
* Favorites
* My Pictures
* Personal
1. Start Regedit
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
3. Double click on any locations you want to change and alter the path
4. Logoff or restart for the changes to go into effect
Eliminating the Right Click on the Taskbar
To eliminate the right click on the taskbar:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
3. Add a DWORD and give it a name of NoTrayContextMenu
4. Give it a value of 1
5. Reboot
Eliminating the Right Click on the Desktop
To eliminate the right click on the desktop:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
3. Add a DWORD and give it a name of NoViewContextMenu
4. Give it a value of 1
5. Reboot
These are only three tricks…..there are many more available on net…..the idea here is not to teach you how to disable right click or how to change the color, fonts, looks, etc…..The basic reason why we post this chapter is to teach that if registry is the place where all the information is stored then why cant we brake passwords from here???
E.g. I install a software on my system to guard some folders which contain material which I want to hide. In order to access the folder I have to input a password, and if it is right only then I can see the content of the folder. From this example it is clear that the password is stored somewhere in the system from where the software compares the value which I enter in the password field. For this example as well as for every other software which asks for password to access the system features including the windows login password, all these values are stored in windows registry. Whenever the user enters a password, it is compared with the value stored in the system registry, and if it is found correct only then the user is allowed to access the feature. In Windows registry we can search for specific items, keys, values or software’s using the search function in edit menu. But there is one problem the password is not stored in its original form, it is converted to some other format so that no one can recognize it. E.g.; If I set the password as “hacking” it is stored as “6167453291” or may be some other form depending upon the software. In such cases what we can do is reset the password i.e. delete the value (whatever it is). Once the value is deleted there is no password and our purpose is solved.
When Windows is not shut down correctly, it will perform an AutoCheck
using CHKDSK on the next restart.
AutoCheck is executed after a short time delay. AutoCheck can be
disabled or delayed by tweaking a few Registry settings.
Run ‘Regedit’ from ‘Start Menu|Run...’
Go to ‘HKEY_LOCAL_MACHINE|SYSTE
M|CurrentControlSet|Control|Session
Manager’.
Create a new DWORD value, or
modify the existing value, called
“AutoChkTimeOut” and set it according
to the value data below.
Value Name: AutoChkTimeOut.
Data Type: REG_DWORD (DWORD Value).
Value Data: Time in Seconds or 0 to disable
(default = 10).
Exit your registry, you may need to
restart or log out of Windows for the
change to take effect.
Monitoring the system
There are various applications you can use to monitor the state of your
system at any given time. One of them is a program called CoolMon (www.coolmon.org) where you can monitor about 22 of
the most geekiest system parameters like the temperature and speed of your system fans, the number of processes running, the total available memory on your hard disk and RAM, CPU utilization, etc. Each
of these can be individually con. gured to appear on the interface. Best of all, this monitoring happens in real time. Better still, the program is free.
If you need more details than what is offered by Windows System Information or the Device Manager, try out an application called Everest Home Edition (www.lavalys.com). This application hunts through your hardware and software setup and extracts every piece of information you might need about your processor, motherboard, graphics card,
hard disk and any other piece of hardware or software information that you might care to know about your computer.
Compress drive to save disk space
its not possible to increase ur memory size but u can compress ur data to save ur disk space, this feature is available in NTFS drive..
if u have a fat or fat32 drive, u can convert it to ntfs by running a command on dos:
for c drive:
convert c:/fs:ntfs
for d drive:
convert d:/fs:ntfs
for e drive:
convert e:/fs:ntfs
run the command similarly if u have more drive...
Compresing data in NTFS
* open my computer
* select any drive(drive with NTFS format)
* right click and select properties
* click on general tab
* select "compress drive to save disk space"
* Apply and OK
ur data will remain safe...
- Changing the Location of Special Folders
You can modify the registry to change the location of special folders like:
* My Documents
* Favorites
* My Pictures
* Personal
1. Start Regedit
2. Go to HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
3. Double click on any locations you want to change and alter the path
4. Logoff or restart for the changes to go into effect
Eliminating the Right Click on the Taskbar
To eliminate the right click on the taskbar:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
3. Add a DWORD and give it a name of NoTrayContextMenu
4. Give it a value of 1
5. Reboot
Eliminating the Right Click on the Desktop
To eliminate the right click on the desktop:
1. Start Regedit
2. Go to HKEY_CURRENT_USER \ Software \ Microsoft \ Windows \ CurrentVersion \ Policies \ Explorer
3. Add a DWORD and give it a name of NoViewContextMenu
4. Give it a value of 1
5. Reboot
These are only three tricks…..there are many more available on net…..the idea here is not to teach you how to disable right click or how to change the color, fonts, looks, etc…..The basic reason why we post this chapter is to teach that if registry is the place where all the information is stored then why cant we brake passwords from here???
E.g. I install a software on my system to guard some folders which contain material which I want to hide. In order to access the folder I have to input a password, and if it is right only then I can see the content of the folder. From this example it is clear that the password is stored somewhere in the system from where the software compares the value which I enter in the password field. For this example as well as for every other software which asks for password to access the system features including the windows login password, all these values are stored in windows registry. Whenever the user enters a password, it is compared with the value stored in the system registry, and if it is found correct only then the user is allowed to access the feature. In Windows registry we can search for specific items, keys, values or software’s using the search function in edit menu. But there is one problem the password is not stored in its original form, it is converted to some other format so that no one can recognize it. E.g.; If I set the password as “hacking” it is stored as “6167453291” or may be some other form depending upon the software. In such cases what we can do is reset the password i.e. delete the value (whatever it is). Once the value is deleted there is no password and our purpose is solved.
Hacking MSN / Yahoo
UPDATED
a small trick ll worked for me hence posting it here
Hacking MSN is actually VERY simple. Msn is designed to route the connection through a microsoft server while you are chatting. However, when a file is sent, a DCC (direct connection) is created. This was purposely done because otherwise microsoft would waste alot of bandwidth so a direct connection is made. This is your chance. Make a file transfer occur between u and a victim (try to send a big file), open up your command prompt (run "cmd" in NT/XP or "command" in 9X to get into prompt) and run netstat. usually the MSN targets IP would be above port 2000. enjoy.
If u recieve some crap like gux1-43.primus.com as the target, do a reverse DNS lookup on it. However, this occurs very rarely, mostly u will recieve a clear IP.
once u have d IP u can do anything with him by Fingerprinting.
U can protect yourself from this occurring to you by using a proxy with MSN (under connections panel in options).
___________________________________________________________________
Beware
The four most common ways of Hacking Yahoo ids are ..\
1.) Social Engineering
2.) Password Crackers
3.) Using Password Stealing Trojans/Keyloggers
4.) Fake Login Pages
Social Enginnering is actually nothing but trying to know your personal and confidential details and then using it to change your password ..BUT HOW? ok there's a forgot password option with Yahoo which asks for your B'day,Country & Zip Code & later your security question..Now generally lamers who try this mode of Hacking have lots of time to waste ..They will put you into some kinda friendship/emotional trap and try to get all the above mentioned information .It may take 1-2 days or even 1-2 month ...(Really I pitty on such lamers !! ).
Tip 1 : Never use your real information while registering on Yahoo(Infact don't use it anywhere on net)
Now if I talk bout a Hacker's perspective...
1.) The most common Security Question is "What's your Pet name?"..Now most of them answer it with very common pet names..I have put on a" names wordlist "in the worldlists section of the site so try those names n m sure u will crack it....Beside this some lamers confuse their NickName with Pet Names ..so if you know their Nick names u may be lucky lol :-)
2.) As far as country is concerned ..try out those countries which you have never heard of (weird names)...lol ( Probably thats what the smart victim thinks when he chooses a country...lmao) & do check Nepal,Phillipines & Bhutan..they r d most common
3.) Zip codes...123456 /007007/ ..something like this ...coz most of the smart victims are very lazy roflmao ...:-)
The second kinda Hacking attempt is done with the Help of Yahoo Password Crackers...I doubt bout their efficiency bt still some of them r lucky (other way round u r stupid lol)..Password Crackers & Password Changers use Brute Force Technique with their updated wordlists...WHAT IS BRUTE FORCE ?I'll make it simple ..it's like using all possible combinations and permutations on the available data and using it as a password ..You can download some frm the Yahoo Tools Section of the site ....Bt again it takes a hell lot of time to crack a password ....
Tip 2: Always use alphanumeric passwords and try to keep it atleast 8 characters long As far as Hacker's perspective is concerned...
Use the worldlist which has victims B'date,phone number,name,zipcode,lucky color,gf's name lol..words like sexy,love,cool,fun,insane,kill,hate & boss ..(You must have these personal informations or else it may take the shit out of u ..trying to hack ...).Beside this generally ppl use their vehicle number,phone number,social security number,credit card number etc as their passwords...
The third and one of the most frequently used way of hacking or stealing Yahoo password is using trojans and keyloggers ..WHAT ARE TROJANS? hmmm..read the tutorial ..I have already wrtten one ...bt still TROJANS are simple programs with a server part and the client part ..you infect the victims computer with the server part and the server then connects to the client running on your system and sends passwords and vital informations..and KEYLOGGERS are programs which record your keystrokes in a log.txt file and sends that log file to the Hacker...
The two most famous Yahoo Password stealing Trojans are Magic PS 1.5 SE ++ ( use google ) & Smart PS 1.5 SE ..once Infected by these trojans the infected server sends your password to the Hackers Yahoo Messenger id as PM 's ...
How to use MAGIC PS 1.5 ?
Ok download MPS.zip then run the mps.exe in it ...you 'll see an user inteface...check the boxes which read"Send Password" & "Send OS name " ...and then gibe an Yahoo id on which you want the Hacked Passwords to be send ..If you want some icon on it then choose the specified icon from the list and then click "Create MPS" .A server.exe will be made in the same folder or in the temp folder in windows ....Send that file to the victim and once he executes it ..Bingo u Have Hacked him/her lol ....
Tip 3: If you see a regsvr.exe file in you windows folder then u r infected ..Also check the system folder(Win98) system 32 (WinXp)...Restart your windows in DOS Mode and delete the file or press CTRL+ALT+DEL and end that process(regsvr.exe){ Not regsvr32.exe it's a system file }or see the list of files from the combo box of MPS client reading" files after install" and then delete it if you find any of them in the windows/system32 folder.Beware sometimes the new MPS creates the server in more than 1 folder.Also look for tapi1314533.exe in your system32 folder( digits after tapi will vary) ** Only solution which will heal it permanently is to install a good antivirus(Norton 2005 /AVG updates/McAfee) are the best.
Tip 4: If u see a flash of PM window disapperaing as you login into you Yahoo & see some probs with the password field(stars changing with dots or vice-versa ).then its party time u r infected ...
Tip 5: Install a good Firewall /Anti-Hacker Program to kill all remote connections or a good freezer which cleans all fresh installations in your primary drive.
As far as Hacker's perspective is concerned...
Pack/Bind the sender.exe (server) so as to make it undetectable by antivirus and then use the flash icon or the setup icon to spoof your victim .Tell him/her that the .exe file is a software patch or some kinda fun stuff and let him/her execute that file...USE THE SEND FILE option of Yahoo messenger for this coz Yahoo mail is protected by Norton so its gonna eat up your server(If nt packed properly).You can also bind the server with some good softwares and then send it but be carefull that the properties of the MPS trojan are not changed (
The last form of Yahoo Password stealing is done by using FAKE LOGIN PAGES ..Now wht the **** :-) is Fake login Page ?These are cloned pages of the real Yahoo Mail Sign in pages .They look very similar to the real conterparts and really very difficult to distinguish..Once you put inyour real id and password and press the submit button you will be either redirected to some other pasge /invalid login page but the trick had already been played by this time ..your id and password would have been mailed to the Hackers mail id by using a 3rd party SMTP server and you don't even realize that you are HACKED...
Tip 6: Always view the address bar ..If the address bar shows something like http://mail.yahoo.com or http://edit.login.yahoo.com then its the authentic page but if its something different then DONOT login.
Tip 7: Some older versions of IE support url redirecting for eg: http://mail.yahoo.com.profile=urid.123455@www.hackeme.com Now the former portion seems to be like the authentic yahoo server address but the page is being redirected to www.hackme.com so check out the URL well...
Tip8: Geocities is NOT YAHOO ..So don't get carried away ....
As far as Hacker's perspective is concerned...
Many free webhosts provide you with a feedback form option or a form mail option .So if you know a bit of HTML you can use their sever is POST ACTION = "" of the Yahoo Fake Page.Just do "Save As " of the real Yahoo page and then edit it form action section with your freeserver's address..But there's a problem..Generally these pages redirect you to THANK YOU PAGES ..So even if you manage to get the password it's of no use coz until and unless the victim is a reall ass lamer he/she would change his/her password after seeing this page ..So the best thing to do is PHP NUKE Now wats dat ?? okie you should know a bit of PHP $ <-- Values and you can code you own mailer.php and call that mailer the PHP on the submit buttons event ..Also dont forget to add some real looking HTML to your mailer the PHP ( may be a INVALID LOGIN PAGE ..)...
Beside this there's always the fear of Physical Hacking ( Some one can juzz sneak in to see your password while you are typin it ) So be carefull..Some ppl do use Password Changers bt thats similar to Password Crackers which I have mentioned above..
Remember this tutorial only teaches the basic terminology behind yahoo password stealing . Hackers are always smarter than you so you never know .....
a small trick ll worked for me hence posting it here
Hacking MSN is actually VERY simple. Msn is designed to route the connection through a microsoft server while you are chatting. However, when a file is sent, a DCC (direct connection) is created. This was purposely done because otherwise microsoft would waste alot of bandwidth so a direct connection is made. This is your chance. Make a file transfer occur between u and a victim (try to send a big file), open up your command prompt (run "cmd" in NT/XP or "command" in 9X to get into prompt) and run netstat. usually the MSN targets IP would be above port 2000. enjoy.
If u recieve some crap like gux1-43.primus.com as the target, do a reverse DNS lookup on it. However, this occurs very rarely, mostly u will recieve a clear IP.
once u have d IP u can do anything with him by Fingerprinting.
U can protect yourself from this occurring to you by using a proxy with MSN (under connections panel in options).
___________________________________________________________________
Beware
The four most common ways of Hacking Yahoo ids are ..\
1.) Social Engineering
2.) Password Crackers
3.) Using Password Stealing Trojans/Keyloggers
4.) Fake Login Pages
Social Enginnering is actually nothing but trying to know your personal and confidential details and then using it to change your password ..BUT HOW? ok there's a forgot password option with Yahoo which asks for your B'day,Country & Zip Code & later your security question..Now generally lamers who try this mode of Hacking have lots of time to waste ..They will put you into some kinda friendship/emotional trap and try to get all the above mentioned information .It may take 1-2 days or even 1-2 month ...(Really I pitty on such lamers !! ).
Tip 1 : Never use your real information while registering on Yahoo(Infact don't use it anywhere on net)
Now if I talk bout a Hacker's perspective...
1.) The most common Security Question is "What's your Pet name?"..Now most of them answer it with very common pet names..I have put on a" names wordlist "in the worldlists section of the site so try those names n m sure u will crack it....Beside this some lamers confuse their NickName with Pet Names ..so if you know their Nick names u may be lucky lol :-)
2.) As far as country is concerned ..try out those countries which you have never heard of (weird names)...lol ( Probably thats what the smart victim thinks when he chooses a country...lmao) & do check Nepal,Phillipines & Bhutan..they r d most common
3.) Zip codes...123456 /007007/ ..something like this ...coz most of the smart victims are very lazy roflmao ...:-)
The second kinda Hacking attempt is done with the Help of Yahoo Password Crackers...I doubt bout their efficiency bt still some of them r lucky (other way round u r stupid lol)..Password Crackers & Password Changers use Brute Force Technique with their updated wordlists...WHAT IS BRUTE FORCE ?I'll make it simple ..it's like using all possible combinations and permutations on the available data and using it as a password ..You can download some frm the Yahoo Tools Section of the site ....Bt again it takes a hell lot of time to crack a password ....
Tip 2: Always use alphanumeric passwords and try to keep it atleast 8 characters long As far as Hacker's perspective is concerned...
Use the worldlist which has victims B'date,phone number,name,zipcode,lucky color,gf's name lol..words like sexy,love,cool,fun,insane,kill,hate & boss ..(You must have these personal informations or else it may take the shit out of u ..trying to hack ...).Beside this generally ppl use their vehicle number,phone number,social security number,credit card number etc as their passwords...
The third and one of the most frequently used way of hacking or stealing Yahoo password is using trojans and keyloggers ..WHAT ARE TROJANS? hmmm..read the tutorial ..I have already wrtten one ...bt still TROJANS are simple programs with a server part and the client part ..you infect the victims computer with the server part and the server then connects to the client running on your system and sends passwords and vital informations..and KEYLOGGERS are programs which record your keystrokes in a log.txt file and sends that log file to the Hacker...
The two most famous Yahoo Password stealing Trojans are Magic PS 1.5 SE ++ ( use google ) & Smart PS 1.5 SE ..once Infected by these trojans the infected server sends your password to the Hackers Yahoo Messenger id as PM 's ...
How to use MAGIC PS 1.5 ?
Ok download MPS.zip then run the mps.exe in it ...you 'll see an user inteface...check the boxes which read"Send Password" & "Send OS name " ...and then gibe an Yahoo id on which you want the Hacked Passwords to be send ..If you want some icon on it then choose the specified icon from the list and then click "Create MPS" .A server.exe will be made in the same folder or in the temp folder in windows ....Send that file to the victim and once he executes it ..Bingo u Have Hacked him/her lol ....
Tip 3: If you see a regsvr.exe file in you windows folder then u r infected ..Also check the system folder(Win98) system 32 (WinXp)...Restart your windows in DOS Mode and delete the file or press CTRL+ALT+DEL and end that process(regsvr.exe){ Not regsvr32.exe it's a system file }or see the list of files from the combo box of MPS client reading" files after install" and then delete it if you find any of them in the windows/system32 folder.Beware sometimes the new MPS creates the server in more than 1 folder.Also look for tapi1314533.exe in your system32 folder( digits after tapi will vary) ** Only solution which will heal it permanently is to install a good antivirus(Norton 2005 /AVG updates/McAfee) are the best.
Tip 4: If u see a flash of PM window disapperaing as you login into you Yahoo & see some probs with the password field(stars changing with dots or vice-versa ).then its party time u r infected ...
Tip 5: Install a good Firewall /Anti-Hacker Program to kill all remote connections or a good freezer which cleans all fresh installations in your primary drive.
As far as Hacker's perspective is concerned...
Pack/Bind the sender.exe (server) so as to make it undetectable by antivirus and then use the flash icon or the setup icon to spoof your victim .Tell him/her that the .exe file is a software patch or some kinda fun stuff and let him/her execute that file...USE THE SEND FILE option of Yahoo messenger for this coz Yahoo mail is protected by Norton so its gonna eat up your server(If nt packed properly).You can also bind the server with some good softwares and then send it but be carefull that the properties of the MPS trojan are not changed (
The last form of Yahoo Password stealing is done by using FAKE LOGIN PAGES ..Now wht the **** :-) is Fake login Page ?These are cloned pages of the real Yahoo Mail Sign in pages .They look very similar to the real conterparts and really very difficult to distinguish..Once you put inyour real id and password and press the submit button you will be either redirected to some other pasge /invalid login page but the trick had already been played by this time ..your id and password would have been mailed to the Hackers mail id by using a 3rd party SMTP server and you don't even realize that you are HACKED...
Tip 6: Always view the address bar ..If the address bar shows something like http://mail.yahoo.com or http://edit.login.yahoo.com then its the authentic page but if its something different then DONOT login.
Tip 7: Some older versions of IE support url redirecting for eg: http://mail.yahoo.com.profile=urid.123455@www.hackeme.com Now the former portion seems to be like the authentic yahoo server address but the page is being redirected to www.hackme.com so check out the URL well...
Tip8: Geocities is NOT YAHOO ..So don't get carried away ....
As far as Hacker's perspective is concerned...
Many free webhosts provide you with a feedback form option or a form mail option .So if you know a bit of HTML you can use their sever is POST ACTION = "" of the Yahoo Fake Page.Just do "Save As " of the real Yahoo page and then edit it form action section with your freeserver's address..But there's a problem..Generally these pages redirect you to THANK YOU PAGES ..So even if you manage to get the password it's of no use coz until and unless the victim is a reall ass lamer he/she would change his/her password after seeing this page ..So the best thing to do is PHP NUKE Now wats dat ?? okie you should know a bit of PHP $ <-- Values and you can code you own mailer.php and call that mailer the PHP on the submit buttons event ..Also dont forget to add some real looking HTML to your mailer the PHP ( may be a INVALID LOGIN PAGE ..)...
Beside this there's always the fear of Physical Hacking ( Some one can juzz sneak in to see your password while you are typin it ) So be carefull..Some ppl do use Password Changers bt thats similar to Password Crackers which I have mentioned above..
Remember this tutorial only teaches the basic terminology behind yahoo password stealing . Hackers are always smarter than you so you never know .....
Winamp Hacking Fr Unlimited Music
Using a loophole in a winamp plugin, you can download and burn music from Napster for free.
music CDs, zero dollars*, obtained legally.
*Not including the cost of blank CDs
Practical how to:
0. Download and install Napster, sign up for 14 day free trial.
1. Download and install Winamp
2. Download and install the Winamp Plug-in Output Stacker
3. Open Winamp Options->Plug-ins->Output->Dietmar's Output Stacker->Configure
a. Add out_ds.dll from Winamp/Plug-ins folder
b. Add out_disk.dll from Winamp/Plug-ins folder
c. Select out_disk.dll in the Output Stacker->Configure
d. Set the output directory and output file mode to Force WAV file
e. Exit preferences
4. Load downloaded Napster protected WMAs into your Winamp playlist
5. Press play and each file will be converted to WAV as it plays
6. Burn WAVs to CD with your favorite burning program
Theoretical fun:
Three computers, one fast networked drive, and a few dedicated people: Turning Napster's 14 day free trial into 252 full 80 minute CDs of free music.
New key developments:
-If you use the "Out-lame" Winamp plugin in the Output Stacker in place of "Out-disk", you can convert straight to MP3. It still encodes no faster than realtime, but this is a great way to conserve space. WAV(Out-disk) is still recommended if you are burning CDs and want to keep as much quality as possible. I can confirm that this all works.
-You can run multiple instances of Winamp at once, each converting its own song. Each instance's playback will not interfere with any of the others, illustrating the fact that this is not simply recording the music off of your soundcard. Doing this, you can get FAR MORE than 252 full 80 minute CDs within 14 days. I can confirm that this works.
You can transcode(MP3) or decode(WAV) X albums in the time it takes for the longest track on the album to elapse. And since you're not limited to only tracks from one album at a time, you can trans/decode as many tracks as instances of Winamp your computer will run limited only by your computer's resources.
Quote from Napster's official statement:
"It would take 10 hours to convert 10 hours of music in this manner."
With the updated methods, you can convert 100 hours or 1,000 hours or 10,000 hours of music in 10 hours. The only limit is your computing resources.
Hack Into a Windows XP Computer Without Changing Password
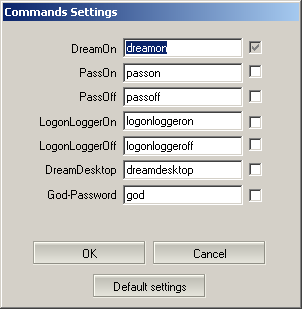
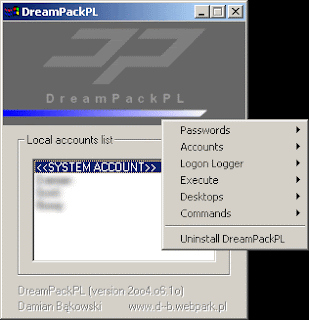
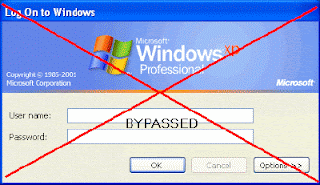
Another method to login to a password protected Windows even if you do not have the password is by making Windows accepting any passwords.
There is a far better way to get into Windows XP. It is easy and it does not reset the password. Hack into a computer running Windows XP without changing the password and find out all and any passwords on the machine (including admin accounts). You do not need access to any accounts to do this. Of course, do not do this on anyone elses computer without proper authorisation.
Steps to Hack into a Windows XP Computer without changing password:
1. Get physical access to the machine. Remember that it must have a CD or DVD drive.
2. Download DreamPackPL HERE.
3. Unzip the downloaded dreampackpl_iso.zip and you'll get dreampackpl.ISO.
4. Use any burning program that can burn ISO images.
5. After you have the disk, boot from the CD or DVD drive. You will see Windows 2000 Setup and it will load some files.
6. Press "R" to install DreamPackPL.
7. Press "C" to install DreamPackPL by using the recovery console.
8. Select the Windows installation that is currently on the computer (Normally is "1" if you only have one Windows installed)
9. Backup your original sfcfiles.dll by typing:
"ren C:\Windows\System32\sfcfiles.dll sfcfiles.lld" (without quotes)
10. Copy the hacked file from CD to system32 folder. Type:
"copy D:\i386\pinball.ex_ C:\Windows\System32\sfcfiles.dll" (without quotes and assuming your CD drive is D:)
11. Type "exit", take out disk and reboot.
12. In the password field, type "dreamon" (without quotes) and DreamPack menu will appear.
13. Click the top graphic on the DreamPack menu and you will get a menu popup.
15. Type "god" in the password field to get in Windows. You can also go to Passwords and select "Logon with wrong password and hash". This option allows you to login with ANY password. Note: I was unable to bring up the DreamPackPL for the first time because I have Kaspersky Anti-Virus already running in background. I believe most antivirus already labelled this tool as a Hack-Tool. A Hack-Tool is NOT a virus. DreamPackPL helps you bypass the Windows Login screen and it is not destructive.
Sunday, July 6, 2008
Monday, June 16, 2008
Byepass the Rapidshare data download limit
This tutorial is on about hacking into rapidshare.de....enjoy!
Rapidshare limits each user to a certain amount of downloading per day based on the users IP address. You can easily cheat rapidshare by showing a different IP address.
How do i change my IP?
1. Clear your browser cookies.
2. Open the command prompt (Start -> Run -> (type) cmd.exe)
3. Run the following simple commands (inorder):
ipconfig /flushdns
ipconfig /release
ipconfig /renew
4. Type exit to close the DOS window. Restart the rapidshare download job.
This trick may not work if your ISP has assigned you a static IP address. (BSNL assigns a dynamic IP)
Rapidshare has blocked my IP?
Note: If Rapidshare blocks your IP, change proxy.
Or: Rapidshare might block an IP from download for sometime. To byepass this restriction, change your IP. First obtain a IP and it’s port from www.publicproxyservers.com Then use that 'IP and port' in your browser Connection settings window. Click OK.
How do i download files from Rapidshare like a Premium user?
Go to a rapidshare download link once the timer is done right click on it and choose FlashGot Link
from the context menu. Flashget will launch the download window. Choose only 1 split file for the download to work. This works on RAPIDSHARE even without a premium account.
Note: If ur on Firefox; Install the Flashgot extension to enable integration of Firefox with Flashget download manager.
Download FlashGet Here: http://filehippo.com/download_flashget/
Rapidshare limits each user to a certain amount of downloading per day based on the users IP address. You can easily cheat rapidshare by showing a different IP address.
How do i change my IP?
1. Clear your browser cookies.
2. Open the command prompt (Start -> Run -> (type) cmd.exe)
3. Run the following simple commands (inorder):
ipconfig /flushdns
ipconfig /release
ipconfig /renew
4. Type exit to close the DOS window. Restart the rapidshare download job.
This trick may not work if your ISP has assigned you a static IP address. (BSNL assigns a dynamic IP)
Rapidshare has blocked my IP?
Note: If Rapidshare blocks your IP, change proxy.
Or: Rapidshare might block an IP from download for sometime. To byepass this restriction, change your IP. First obtain a IP and it’s port from www.publicproxyservers.com Then use that 'IP and port' in your browser Connection settings window. Click OK.
How do i download files from Rapidshare like a Premium user?
Go to a rapidshare download link once the timer is done right click on it and choose FlashGot Link
from the context menu. Flashget will launch the download window. Choose only 1 split file for the download to work. This works on RAPIDSHARE even without a premium account.
Note: If ur on Firefox; Install the Flashgot extension to enable integration of Firefox with Flashget download manager.
Download FlashGet Here: http://filehippo.com/download_flashget/
Rapidshare cheats
Rapidshare cheats
If you are looking for rapidshare cheats than we have got some excellent rapidshare cheats for your pleasure.
In your windows Go to Start > Run and then type cmd
On Command prompt type as follows:
type > ipconfig /flushdns < ---Enter
type -----> ipconfig /release < ---Enter
type -----> ipconfig /renew < ---Enter
type -----> exit < Enter
If you Ip address as alloted by your ISp id dynamic then this cheat will work otherwise this rapid share cheat will not work.
If you are looking for rapidshare cheats than we have got some excellent rapidshare cheats for your pleasure.
In your windows Go to Start > Run and then type cmd
On Command prompt type as follows:
type > ipconfig /flushdns < ---Enter
type -----> ipconfig /release < ---Enter
type -----> ipconfig /renew < ---Enter
type -----> exit < Enter
If you Ip address as alloted by your ISp id dynamic then this cheat will work otherwise this rapid share cheat will not work.
Thursday, February 21, 2008
DIY Remote Camera Trigger
DIY web site Instructables details how to turn a $3 hands-free phone headset into a remote shutter trigger for your digital camera. The trigger described in the tutorial should work with most digital cameras with a 2.5mm plug for remote triggering (including the popular Canon Rebel). From start to finish the project takes about five minutes, and you can't beat the price. We've highlighted a much more involved remote trigger in the past, so if for some reason this method won't work for you and you're willing to roll up your sleeves, you might want to give that a look.
INTERNET SITES (FREE APPS,SONGS etc)
pakkadesi.com
xsharex.info
desipunjabis.net
mobile420.com
Wallpaperpacks.com
HINDIMELODY.TK
DESIMASALA.INFO
I3GP.COM
http://www.windows-vista-stuff.com
http://www.themejunkie.com
http://www.thefreepicture.com/
http://desipunjabis.net
http://www.desifunda.net
www.getsymbian.com
WWW.WAREZDONKRY.COM
http://www.nokiagamez.net/
soft.mobilesmania.com
http://www.crazy4mobilez.com
simtel.net
www.allxperts.info
www.koolhere.com
www.koolpoetry.com
www.pakmates.com
www.funnyhits.com
www.kooldreams.com
www.apnakhanewal.com
www.bestsymbian.com
http://www.protorrent.com
SOFT32.COM
www.songs.pk
musicnmovies.com
thirtythree.tech
mp3hungama.com
papuyaar.com
download3000.com
crackfound.com
divxcrawler.com
mobango.com
pz10.com
www.bollyplaza.tk
apunkabollywood.com
www.software.com
Okesite.com
www.youtube.com
mobango.com
free-3gp-video.com
http://www.funplusfun.com
http://smartforumz.org
www.daily-warez.org
www.maxgrab.org
www.softarchive.net
softzone.org
CyprusZone.com
forums.top-stuff.info
keygen.us
www.forumwz.org
crack0hack.wetpaint.com
WWW.JEYJEY.BLOGFA.COM
katz.cd
katzforums.com
donkeywarez.com
www.Demonoid.com
http://www.hellorapid.com
http://www.rsrip.com
http://www.rapidl.com
http://rsdownload.com
downloadcenter.com
http://fireav.com/downloads/
www.safer-networking.org
www.joost.com/download/
www.gamerzplanet.net
www.thetechguide.com
www.cyberwarez.info
www.mastiland.com
http://www.geocities.com/mp3malayalamsongs/
forum.cmszone.org
PaulpBaker.COM
FORUMMASTI.COM
www.forumdownload.com/
BeebaMunda.Peperonity.Com
Desiflea.co.uk
www.final4ever.com
WZor.Net
www.nokiasoftware.net
http://www.od3n.net/tools/
nokiamasti.com
airtelnop.com
xsharex.info
desipunjabis.net
mobile420.com
Wallpaperpacks.com
HINDIMELODY.TK
DESIMASALA.INFO
I3GP.COM
http://www.windows-vista-stuff.com
http://www.themejunkie.com
http://www.thefreepicture.com/
http://desipunjabis.net
http://www.desifunda.net
www.getsymbian.com
WWW.WAREZDONKRY.COM
http://www.nokiagamez.net/
soft.mobilesmania.com
http://www.crazy4mobilez.com
simtel.net
www.allxperts.info
www.koolhere.com
www.koolpoetry.com
www.pakmates.com
www.funnyhits.com
www.kooldreams.com
www.apnakhanewal.com
www.bestsymbian.com
http://www.protorrent.com
SOFT32.COM
www.songs.pk
musicnmovies.com
thirtythree.tech
mp3hungama.com
papuyaar.com
download3000.com
crackfound.com
divxcrawler.com
mobango.com
pz10.com
www.bollyplaza.tk
apunkabollywood.com
www.software.com
Okesite.com
www.youtube.com
mobango.com
free-3gp-video.com
http://www.funplusfun.com
http://smartforumz.org
www.daily-warez.org
www.maxgrab.org
www.softarchive.net
softzone.org
CyprusZone.com
forums.top-stuff.info
keygen.us
www.forumwz.org
crack0hack.wetpaint.com
WWW.JEYJEY.BLOGFA.COM
katz.cd
katzforums.com
donkeywarez.com
www.Demonoid.com
http://www.hellorapid.com
http://www.rsrip.com
http://www.rapidl.com
http://rsdownload.com
downloadcenter.com
http://fireav.com/downloads/
www.safer-networking.org
www.joost.com/download/
www.gamerzplanet.net
www.thetechguide.com
www.cyberwarez.info
www.mastiland.com
http://www.geocities.com/mp3malayalamsongs/
forum.cmszone.org
PaulpBaker.COM
FORUMMASTI.COM
www.forumdownload.com/
BeebaMunda.Peperonity.Com
Desiflea.co.uk
www.final4ever.com
WZor.Net
www.nokiasoftware.net
http://www.od3n.net/tools/
nokiamasti.com
airtelnop.com
Saturday, February 16, 2008
Deadly Desire (Francesca Cahill Romance Novels)

Deadly Desire (Francesca Cahill Romance Novels)
By Brenda Joyce
* Publisher: St. Martin’s Paperbacks
* Number Of Pages: 352
* Publication Date: 2002-05-19
* Sales Rank: 274720
* ISBN / ASIN: 0312982631
* EAN: 9780312982638
* Binding: Mass Market Paperback
* Manufacturer: St. Martin’s Paperbacks
* Studio: St. Martin’s Paperbacks
* Average Rating: 4
* Total Reviews: 32
Book Description:
Brenda Joyce has enthralled millions of readers with her New York Times bestelling novels. Now, join us in the next chapter of her unforgettable storytelling: the Francesca Cahill novels, written as B.D. Joyce. Embark on an adventure of danger and romance and let yourself be transported to another era where your senses will be stimulated and your emotions stirred….DEADLY DESIREThe time is turn-of-the-century New York City. Society’s elite hosts glittering balls inside sprawling mansions while outside, the teeming streets harbor secrets of their own.New York City’s Police Commissioner Rick Bragg has been called upon to investigate a shocking crime. Reluctant to pull Francesca into a case that could be very dangerous, Rick also knows the beautiful and brilliant heiress has a natural ability for sleuthing that could aid him-even if it means working side by side with a woman who tempts him like no other. And so Francesca and Rick begin a harrowing journey through the squalid underworld of the city that plunges them deeper and deeper into a peril neither could have imagined-and a desire that only continues to grow….
Download
HTML: Your Visual Blueprint For Designing Effective Web Pages

HTML: Your visual blueprint for designing effective Web pages
By Ruth Maran
* Publisher: Visual
* Number Of Pages: 350
* Publication Date: 2000-07-01
* Sales Rank: 264060
* ISBN / ASIN: 0764534718
* EAN: 0785555030572
* Binding: Paperback
* Manufacturer: Visual
* Studio: Visual More...Book Description:
Welcome to the only guidebook series that takes a visual approach to professional-level computer topics. Inside you'll discover step-by-step screen shots that demonstrate over 100 key HTML tasks, including:
* Setting up a Web page
* Reducing image resolution
* Creating a link to an FTP site
* Adding an embedded sound
* Creating radio buttons
* Creating an inline frame
* Adding JavaScript to a Web page
* Adding a hit counter
* Creating an internal stylesheet
* Creating an XML declaration
The companion CD-ROM includes:
* HomeSite, Gif.gIf.giF, and Paint Shop Pro evaluation versions
* Goldwave, CuteFTP, and WS_FTP Pro shareware trials
* BBEdit 5.1.1 demo
* Plus, all sample code and an eversion of the book
Download
A Beginner’s Guide to (X)HTML, StyleSheets, and Web Graphics

Publisher O’Reilly
Author(s) Aaron Gustafson
ISBN 0596527527
Release Date 29 June 2007
Everything you need to know to create professional web sites is right here. Learning Web Design starts from the beginning — defining how the Web and web pages work — and builds from there. By the end of the book, you’ll have the skills to create multi-column CSS layouts with optimized graphic files, and you’ll know how to get your pages up on the Web.
This thoroughly revised edition teaches you how to build web sites according to modern design practices and professional standards. Learning Web Design explains:
* How to create a simple (X)HTML page, how to add links and images
* Everything you need to know about web standards — (X)HTML, DTDs, and more
* Cascading Style Sheets — formatting text, colors and backgrounds, using the box model, page layout, and more
* All about web graphics, and how to make them lean and mean through optimization
* The site development process, from start to finish
* Getting your pages on the Web — hosting, domain names, and FTP
The book includes exercises to help you to learn various techniques, and short quizzes to make sure you’re up to speed with key concepts. If you’re interested in web design, Learning Web Design is the place to start.
Download Your eBook Now
Download eBook
Download from rapidshare.de
Download eBook
Leonardo Da Vinci - The Madrid Codices 1

Leonardo Da Vinci - The Madrid Codices I
Ebook | PDF | Italian | Year 1493 | Facsimile (Year 1974, McGraw-Hill Book Company) | 22 files, 710 Mb total, 410 pages total | RapidShare
The Codex Madrid I was rediscovered in 1966 together with the Codex Madrid II. This is a bound volume with precise, carefully worked drawings concerning mainly the science of mechanisms.
Priority is given to the drawings, which are accompanied by a commentary or a caption. The care taken with the layout of each individual page and the finesse of the drawings indicates that the drawings are close to publishable form, either as a presentation manuscript or printed treatise.
RapidShare folder
http://rapidshare.com/users/XKJ0O5
DEATH : The Final Mystery

DEATH : The Final Mystery
Dundurn Press| 2000 | ISBN 0888822219 | English | 249 pages | PDF | 2.23 MB
The greatest human problem is that we are all born in the condemned cell. Money and medical science can extend the human lifespan significantly — perhaps up to one thousand years via cloning and cryogenics — but in the end, when the last medical miracle has been exhausted, Death still waits patiently for us. In Death: The Final Mystery, Lionel and Patricia Fanthorpe take their investigative skills to those last moments of life and beyond, exploring such puzzling topics as near-death and out-of-body experiences, reincarnation theories, hypno-regression, and automatic writing and other phenomena of the s?ance room. Evidence is drawn from trance mediums, the writings of mystics, and clear, hard facts reported by reliable eyewitnesses.
DOWNLOAD
SQL: A Beginner's Guide, Second Edition

Paperback: 560 pages
Publisher: McGraw-Hill Osborne Media; 2 edition (April 28, 2003)
Language: English
ISBN-10: 0072228857
ISBN-13: 978-0072228854
Here is the foundation upon which you can build your relational database design and programming, then apply those skills to any SQL-based product. Carefully organized for beginners, you’ll learn step-by-step how to create a database, create tables, enforce data integrity, query and modify data, and implement advanced data access techniques.
File Size : 7.07 MB
Download Ebook : http://w15.easy-share.com/15659971.html
Installing, Troubleshooting, and Repairing Wireless Networks

Paperback: 398 pages
Publisher: McGraw-Hill/TAB Electronics; 1 edition (March 24, 2003)
Language: English
ISBN-10: 0071410708
ISBN-13: 978-0071410700
This book/CD-ROM package is THE definitive reference to the benefits, pitfalls, set-up, troubleshooting, and repair of wireless networks. The author covers the entire range of wireless networks and explains the specific needs of each individual application.
* Introduces all the various wireless system components—both “off the shelf” and subscriber
* Covers essential technologies such as 802.11a and b, Bluetooth, and 3G cellular phone systems
* Provides solutions for interference, range, and throughput problems
* CD-ROM includes software tools and utilities to assist with connections, diagnostics, troubleshooting, and repair
File Size : 4.57 MB
Download Ebook : http://w15.easy-share.com/15659641.html
Friday, February 15, 2008
Digital Photo Magazine CD Content Oct 2007 - Photoshop for Perfect Portraits | 330 MB

Digital Photo Magazine CD Content Oct 2007 - Photoshop for Perfect Portraits | 330 MB
you’ll discover how to take and make brilliant fine-art pictures using your digital camera and software. We’ll show you how to create moody mono shots, make sumptuous textured portraits, add text and arty borders to your shots and even turn regular photos into paintings! You’ll also find out how to create amazing pop-art portraits of your friends and family! plus 40 texture effects - and by following the video lesson on this CD, you’ll discover how they can be used individually or in combination with other textures to create dramatic arty effects.
http://rapidshare.com/files/63885340/DPCD.part1.rar
http://rapidshare.com/files/63919118/DPCD.part2.rar
http://rapidshare.com/files/63046789/DPCD0ct07.part3.rar
http://rapidshare.com/files/63060399/DPCD0ct07.part4.rar
The Principles of Beautiful Web Design

The Principles of Beautiful Web Design
# Author:Jason Beaird
# Format:PDF 7.0MB
# Page Count: 180 pages
# Publisher: SitePoint; 1 edition (January 31, 2007)
# Language: English
# ISBN-10: 0975841963
# ISBN-13: 978-0975841969
Tired of making web sites that work absolutely perfectly but just don't look nice?
If so, then The Principles of Beautiful Web Design is for you. A simple, easy-to-follow guide, illustrated with plenty of full-color examples, this book will lead you through the process of creating great designs from start to finish. Good design principles are not rocket science, and using the information contained in this book will help you create stunning web sites.
# Understand the design process, from discovery to implementation
# Understand what makes "good design"
# Developing pleasing layouts using grids, the rule of thirds, balance and symmetry
# Use color effectively, develop color schemes and create a palette
# Use textures, lines, points, shapes, volumes and depth
# Learn how good typography can make ordinary designs look great
# Effective imagery: choosing, editing and placing images
# And much more
Throughout the book, you'll follow an example design, from concept to completion, learning along the way.
Download 下载
[Rapidshare] The.Principles.of.Beautiful.Web.Design.Jan.2007.eBook-BBL.rar
SEO: Search Engine Optimization Bible

This in-depth Bible delivers the holy grail of online marketing: how to influence search engine results to drive online shoppers to specific Web sites; the process is called search engine optimization (SEO) and it is a hot topic
One-stop resource offers readers what they need to plan and implement a successful SEO program, including useful tips on finding the shortest routes to success, strategy suggestions, and sidebars with more information and additional resources
Features interviews with executives from top search companies, plus appendices on creating successful listings with Google, MSN, Yahoo!, and others
Topics include creating an SEO plan; managing keywords; maximizing pay-per-click strategies; understanding the role of links and linking; robots, spiders, and crawlers; maintaining SEO; analyzing success rates; and much more
http://mihd.net/6g5m82
http://rapidshare.com/files/91368198/0470175001.7z
Networking with Microsoft Windows Vista: Your Guide to Easy and Secure Windows Vista Networking

Your Guide to Easy and Secure Windows Vista Networking is a complete beginner’s guide to creating, configuring, administering, and using a small network using Windows Vista computers. Inside you’ll find comprehensive coverage of networking hardware, including Ethernet (wired) hardware (from NICs to cables to switches to routers) and wireless Hardware–from wireless NICs to access points to range extenders.
We include handy âbuyer’s guidesâ that tell you how to make smart choices when purchasing network hardware. With hardware in hand, we then show you how to roll up your shirtsleeves and put everything together, including configuring a router, laying cable, and connecting the devices. Next, we then show you how to wrangle with Windows Vista’s networking features. These techniques include using the Network and Sharing Center, managing wired and wireless connections, accessing shared network resources, sharing local resources on the network, and working with network files offline. And if you are a music and video aficionado, we’ve got you covered with a special chapter that shows you just how to set up a networked Vista PC as your digital media hub!
No networking book would be complete without extensive coverage of security issues that affect anyone connected to the Internet. We show you how to secure each computer, secure your global networking settings, and batten down your wireless connections. The last part of the book includes intermediate networking tasks such as
making remote connections, monitoring the network, troubleshooting network problems, and setting up Vista’s built-in web server and FTP server.
• No longer is networking a topic that only geeks need to understand.
If you have even one computer on the Internet or if you use wireless
in your home or office, you need this book!
• Extensive hardware coverage that shows you what equipment to
buy and how to set it up!
• Easy to follow buyer’s guides that enable anyone to make smart
and informed choices when purchasing networking hardware.
• Complete and comprehensive coverage of Windows Vista’s
networking features.
• Thwart hackers, crackers, thieves and other Internet malefactors
by following our easy to understand chapters on security!
• Loaded with tips, tricks, and shortcuts to make networking easier
and more secure.
• Chock full of real-world examples and network configurations that
you can put to work today!
http://mihd.net/ip6hx1
http://rapidshare.com/files/85241761/0789737779.rar
Patterns in Network Architecture: A Return to Fundamentals

In Patterns in Network Architecture, pioneer John Day takes a unique approach to solving the problem of network architecture. Piercing the fog of history, he bridges the gap between our experience from the original ARPANET and today’s Internet to a new perspective on networking. Along the way, he shows how socioeconomic forces derailed progress and led to the current crisis.
Beginning with the seven fundamental, and still unanswered, questions identified during the ARPANET’s development, Patterns in Network Architecture returns to bedrock and traces our experience both good and bad. Along the way, he uncovers overlooked patterns in protocols that simplify design and implementation and resolves the classic conflict between connection and connectionless while retaining the best of both. He finds deep new insights into the core challenges of naming and addressing, along with results from upper-layer architecture. All of this in Day’s deft hands comes together in a tour de force of elegance and simplicity with the annoying turn of events that the answer has been staring us in the face: Operating systems tell us even more about networking than we thought. The result is, in essence, the first “unified theory of networking,” and leads to a simpler, more powerful–and above all–more scalable network infrastructure. The book then lays the groundwork for how to exploit the result in the design, development, and management as we move beyond the limitations of the Internet.
Using this new model, Day shows how many complex mechanisms in the Internet today (multihoming, mobility, and multicast) are, with this collapse in complexity, now simply a consequence of the structure. The problems of router table growth of such concern today disappear. The inescapable conclusion is that the Internet is an unfinished demo, more in the tradition of DOS than Unix, that has been living on Moore’s Law and 30 years of band-aids. It is long past time to get networking back on track.
• Patterns in network protocols that synthesize “contradictory” approaches and simplify design and implementation
• “Deriving” that networking is interprocess communication (IPC) yielding
• A distributed IPC model that repeats with different scope and range of operation
• Making network addresses topological makes routing purely a local matter
• That in fact, private addresses are the norm–not the exception–with the consequence that the global public addresses required today are unnecessary
• That mobility is dynamic multihoming and unicast is a subset of multicast, but multicast devolves into unicast and facilitates mobility
• That the Internet today is more like DOS, but what we need should be more like Unix
• For networking researchers, architects, designers, engineers
Provocative, elegant, and profound, Patterns in Network Architecture transforms the way you envision, architect, and implement networks.
http://mihd.net/w4s09o
http://rapidshare.com/files/88919210/0132252422.rar
Managing IP Networks

IP has a major role in the evolution of networks and services. Issues relating to end-to-end network and service management which offers advanced services, are addressed in this book; making it a defining work on this topic.
http://mihd.net/34d57j
http://www.filefactory.com/file/f7540c/
Cisco Certified Network Associate (CCNA)

To become a Cisco Certified Network Associate (CCNA), you must learn the hundreds of IOS commands used by Cisco routers and switches. This handy reference from Cisco networking authority Todd Lammle is just what you need to master those commands. From a thorough introduction to Cisco’s basic operating system to making the transition to IPv6, Todd Lammle walks you through hundreds of commands with short, to-the-point explanations and plenty of figures and real-world examples.
http://mihd.net/j071oi
http://rapidshare.com/files/91372280/0470175605.7z
Ubuntu Linux - Get free CDs

Ubuntu is a free, open source Linux Operating System based on Debian Linux. This flavor of Linux focuses on the User Friendliness and usability of Linux. In spite of being open source, Ubuntu team is dedicated to provide support at least for 18 months after a particular release of Ubuntu.
Also Ubuntu is the most preferred flavor of Linux in this world. And Ubuntu support both x86 and Sun sparc architectures. So that you can run Ubuntu even on Sun Hardwares. In order to increase the popularity, the Ubuntu team is giving away free copies of Ubuntu Linux either by download or by free CDs.
Don't get excited.. its true. They are giving away free CDs. You can get it from here.
Get coupon codes for amazon, ebay and many other online stores

Here is a great opportunity for online buyers through amazon , eBay and many other shopping sites. RetailMeNot is a web site through which they provide the coupon codes for amazon, eBay, papajohns, ae.com, gap.com, kohls.com and many more e-commerce sites.
With these coupon you may get even upto 50% discount on your order. If you don't use, you may pass on this information to your friends and relatives so that they will get benefited.
Visit RetailMeNot.com today and get more discounts on your online orders in eBay, amazon and many other online stores.
Download videos from YouTube, Google Videos, Yahoo Videos, ifilm, metacafe with new realplayer

You can find different approaches for downloading your favorite videos from YouTube, just by googling it. Here is a new approach for downloading is not only applicable to YouTube, but its applicable to all similar sites like Google videos, Yahoo videos, ifilm, metacafe etc.
It is very simple way of downloading flash videos from internet. Only thing you need to do is to install latest RealPlayer and enable the plugins that are coming for both internet explorer and Firefox (by default these plugins will be enabled).
Once you are done with the installation you need to restart your web browsers and then visit any of the favorite videos in YouTube, Google videos, Yahoo Videos, ifilm, metacafe etc and just keep the mouse pointer over the video that is playing. Now, you will get a menu for downloading that particular flash video using RealPlayer.
Just click and download. Done!. Now you have your favorite video from YouTube in your personal computer. Either you can install free FLV players available or you can install the FLV plugin for Windows Media Player.
Download all New RealPlayer 11.
Orkut Cute - Free Scrap Software for Orkut and other Communities

Orkut Cute is a free software from APC Software which can help you to send scraps to all your friends in Orkut and all your other online social networking communities. This software also informs you when ever you receive new scrap(s) or new topics from your communities.
Get Orkut Cute
Successful ways of blog and website promotion

Many bloggers and webmasters has to work a lot for getting their site or blog get noticed by more number of people over internet. There are number of ways for promoting and building traffic to your website and blog. Some methods of promotion are free and some are paid.
Here are some common methods for promoting blog or website
* Add your blog name or website with signature of mail and in visiting card
* Update your blog name or website in social networking sites like orkut, myspace etc.
* Add your blog name or website in GTalk and Yahoo Messenger titles.
* Register in DMOZ directories.
* Submit your blog name or website in search engines.
* Register your blog name or website in blog directories.
* Do link exchange with people with similar ranks and traffic.
* Join discussion forums and add your blog name or website name as signature.
* Use Twitter.com and publish your updates.
* If your blog or website targets localized customers then put banners on back of taxi and buses. Also you can set the home page of computers internet cafes in a particular area with your website or blog (Make sure to have a good relation with Cafe owner).
There are also some tips for promotion and building traffic by Liz Strauss at successful-blog.com which will be very useful for most of the people.
How blogger play will help your blog get famous

Blogger team has recently launched a new photo sliding portal for blogger. The portal named play.blogger.com will take care of showing the latest images uploaded by bloggers on blogspot platform dynamically. One pretty thing is that, they also link to the blog in which the image is displayed.
So If you have posted an article with a relevant image, it is sure that some people who are viewing play.blogger.com will see it and will visit your blog. Thus you will get more readers to your blog just being on blogspot platform.
But, you have to remember that they will show images only after applying family filters.
Download free professional blogger templates
Here are some websites that offers free professional blogger templates for you. You can download the complete template code and customize it as your wish.
http://thrbrtemplates.blogspot.com/
http://freeblogspottemplates.blogspot.com/
http://www.blogskins.com
http://blogger-templates.blogspot.com/
http://blogtemplates.noipo.org/
These sites contains templates for both old and new blogger also for the wordpress
blogs. Enjoy and share with your friends.
http://thrbrtemplates.blogspot.com/
http://freeblogspottemplates.blogspot.com/
http://www.blogskins.com
http://blogger-templates.blogspot.com/
http://blogtemplates.noipo.org/
These sites contains templates for both old and new blogger also for the wordpress
blogs. Enjoy and share with your friends.
How to add more than 1000 friends in Orkut
When I was going through some of the profiles in Orkut, I found that some of the profiles have more than 1000 friends in their friends list. But, I heard that Orkut itself has imposed a restriction that, an Orkut member can have maximum of 1000 friends in his friends list.
If that is the case, then how could some people alone can have more than 1000 friends in their friends list?.
I went through some of the profiles with more than 1000 friends in their friends list, and no one were directly related to Google. Then I googled for a solution to add more than 1000 friends in my Orkut friends list. And I found out an interesting article at OrkutPlus.BlogSpot.com which suggests some ways for adding more than 1000 friends in Orkut friends list.
If that is the case, then how could some people alone can have more than 1000 friends in their friends list?.
I went through some of the profiles with more than 1000 friends in their friends list, and no one were directly related to Google. Then I googled for a solution to add more than 1000 friends in my Orkut friends list. And I found out an interesting article at OrkutPlus.BlogSpot.com which suggests some ways for adding more than 1000 friends in Orkut friends list.
Latest Firefox with fix for Cross Site Scripting (XSS)

Cross Site Scripting was one of the major security threat faced by internet users. This security vulnerability may be exploited to allow code injection by malicious web users into the web pages viewed by other users.
Now Firefox users can stay safe as this vulnerability has been fixed in the latest release of the Firefox web browser. There are couple of other security fixes that are made in the latest release, Firefox 2.0.0.12.
* Web forgery overwrite with div overlay
* URL token stealing via style-sheet redirect
* Mishandling of locally-saved plain text files
* File action dialog tampering
* Web browsing history and forward navigation stealing
* Directory traversal via chrome: URI
* Stored password corruption
* Privilege escalation, XSS, Remote Code Execution
* Multiple file input focus stealing vulnerabilities
* Crashes with evidence of memory corruption
Its another reason to switch to Firefox, for non Firefox users and time to update your web browser for old Firefox users.
Suggested post: Download Free Security Software for Your Personal and Business Computers
Valentine Wishes in Google Way
Thursday, February 14, 2008
continued "Quickly Compose New Gmail Messages with Launchy"
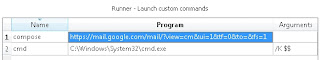
Hit the "+" button under the main box, and your cursor is placed in the "Name" box. Type in whatever word you want to type into Launchy to open a new Gmail composition—I used "compose," like Samar suggested, but you can adapt to whatever gets you to there quickest in Launchy.
Now for the secret sauce. In the "Program" field to the right of "Name," paste in this line:
https://mail.google.com/mail/?view=cm&ui=1&tf=0&to=&fs=1
Leave the "Arguments" field blank, and it should all look like this (with the "Program" field re-sized):
launchy_options2.jpg
Hit "OK," and you're all set. Type in "Compose" or whatever your shortcut name was. Got your own Launchy/Gmail hacks and tweaks? Share them in the
Quickly Compose New Gmail Messages with Launchy

Lifehacker reader Samar liked the quick-write convenience of the GmailThis bookmarklet, but wanted to dig deeper to find a solution that would both work with his (and our own) favorite Windows keyword launcher, Launchy, and run whether or not Firefox (or any default Windows browser) was already open. We're glad he did, because he's come up with a one-line command that lets you open new Gmail composition windows from anywhere. The tip, and screenshots, after the jump.
First off, take note that this trick will only be convenient if you keep yourself logged into Gmail on a regular basis. But if you use both Gmail and Launchy on a regular basis, it's a pretty simple hack that can make Gmail feel as fast as a desktop mail app
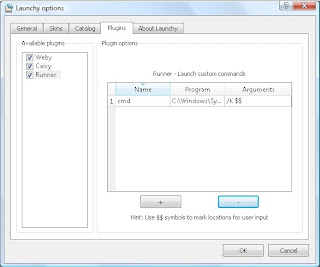
Open a Launchy window and click to open the options dialog (the "gear" in the upper-right corner in the default 2.0 skin). Once there, head to the "Plugins" tab and click the "Runner" plugin. If you've never touched the Runner plugin before, you should see one command shortcut there, "cmd."
Top iTunes Smart Playlists

One of iTunes' most powerful and useful features is Smart Playlists: dynamic, search-based lists of songs that save you the work of grouping tunes by hand. But with almost 40 fields to search against—from Album and Artist to Bit Rate and Category—there are thousands of possible Smart Playlist combinations. If you listen to music while you work, but don't want to waste time manually creating playlists in iTunes, today we've got our top 10 favorite Smart Playlists that will keep your tunes fresh and focused automatically.
Monitor Web Sites for Updates with Update Scanner

Firefox only (Windows/Mac/Linux): The Update Scanner Firefox extension monitors web sites and alerts you whenever the site updates its content. While RSS feeds have put an end to your days constantly refreshing most sites worth their salt, there are still web pages that lack feeds that you may want to keep an eye on. Like what? Like a company's job page, for example, or just sites you love that remain a little behind the curve. You can even adjust scanning intervals and "change thresholds" so insignificant changes are ignored. Update Scanner is free, works wherever Firefox does.
Update Scanner [Firefox Add-ons via Extend Firefox]
Create Quick FedEx Shipments from Outlook with QuickShip

Windows only: FedEx QuickShip is a freeware Microsoft Outlook toolbar that integrates your Outlook address book with FedEx shipments. That means creating a new shipment is as easy as clicking Ship and choosing your contact's name from your address book. You can also track packages, check shipping rates, schedule pickups, find FedEx locations, and more with the FedEx toolbar. As Download Squad points out, the tool could use even tighter integration (for example, recognizing tracking numbers in emails), but if you do a lot of shipping at work and Outlook is your go-to email client, the QuickShip toolbar is a must-have. QuickShip is freeware, Windows only.
QuickShip [FedEx via Download Squad]
Wednesday, February 13, 2008
Web site iWebSaver saves entire web pages to your iPhone or iPod touch by converting the entire page to a data URL, then providing that data link as a

Web site iWebSaver saves entire web pages to your iPhone or iPod touch by converting the entire page to a data URL, then providing that data link as a bookmark you can save to your bookmarks or your home screen. That means next time you're about to jump on a plane or hit the tunnel on the train, you can use iWebSaver to save some reading material directly to your device before you lose your signal. One would think you could do this just by loading the web pages in beforehand, but Safari often reloads pages inactive, so that's not a foolproof method. iWebSaver ensures you've got some reading material saved directly to your device. Be sure to bookmark the iWebSaver
Tuesday, February 12, 2008
Mobile Secret Codes
Nokia 31xx
____________
Firmware version
*#0000# or *#3110#
IMEI Code
*# 06 #
Restores Factory Settings
*#7780#
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Nokia 5110
_____________
IMEI Number *#06#
For checking the IMEI (International Mobile Equipment Identity).
---------------------------------------------------------
Security Code 12345
Default security code is 12345. If you forgot your security code, there s so many program on the net which allowed you to know the security code likes Security ID Generator, Nokia IMEI Changer, etc.
update:
Security ID Generator (SID.EXE) and IMEI Generator (NOKIAIMEI.EXE) doesn t works with Nokia 5110
Resetting Security Code
If you accidentally lock the phone or forgot the security code, the best thing to do is check it with your local Nokia dealer. For advanced user, you can use WinTesla, PCLocals or LogoManager program to read the security code or resetting the code (You will need an FBUS/MBUS (or compatible) cable to do this.
---------------------------------------------------------
Software Version *#0000#
For checking the phones software (SW) - called firmware revision information.
e.q : Version V. 4.51 (26-03-98) will display
V 04.51
26-03-98
NSE-1
first line:
The Software Version (my guess is that this software has been used in previously Nokia-phones, what do you say?!).
second line:
The Date of the SW release.
third line:
NHE-8 has something to do with the type of phone you are dealing with. Is it GSM 900 (standard), GSM 1800 (DCS1800) or GSM 1900 (PCS1900)?
Nokia 2110, 3110, 8110(i) are all NHE types. The only thing that vary is the code after NHE- ("8").
NHE = GSM 900, NHK =GSM 1800 - The number in the end = the model (2110i = 4 etc.)
The 5110 and 6110 is called NSE-1 and NSE-3...this may be because it supports EFR (?)
update:
Newest Software Version was V5.22 (xx-xx-99)
V 05.22
01-07-99
NSE-1
If your software version is V4.00, upgrade your software version to latest version. V4.00 contains bugs that sometimes will show message,
"SIM Card Not Ready" even the card is already inside the phone.
---------------------------------------------------------
Software Update
The only thing to do (for you and me) is for us to go to the nearest Nokia dealer and make him do it for you. Just remember that it is supposed to be free (a receipt is required) so don t let him tell you anything else!
---------------------------------------------------------
SIM clock *#746025625# [*#sim0clock#]
to check if the Sim-Clock can be Stopped. This option is depen on your service provider network. (Sim-clock-stop is a kind of standby mode which will save battery time)
update:
This code doesn t work on phone with software version 4.59.
---------------------------------------------------------
Waranty Code *#92702689# [*#war0anty#]
Menu:
Displays Serial Number.
Displays the Month and Year of Manufacture (0698)
Displays (if there) the date where the phone was purchased (MMYY) you can here set the Purchasing Date
(Warning: You can only do this once - so be careful what you write)
Displays the date of the last repairment - if found (0000)
The next screen has Transfer User Data? (the same option as the 8110)
To exit turn the phone off and then back on.
---------------------------------------------------------
SP Lock The Service provider (SP) lock
Is used to lock the cell phone to the SP s SIM card. Once the cell phone is locked to a specific operator, if one inserts a SIM card from a different operator the phone will refuse to accept it!
The cell phone will however accept another SIM card from the same operator.
All Nokia phones (2110 and newer) have four different SIM locks which can be used to lock the phone for up to 4 different providers. But most phones with restriction only have one lock activated. ( lock 1)
The main code used in Nokia phones is:
#pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
(I can NOT give you the master code SO DON T ASK ME FOR IT! )
Please click here to learn more about how to obtain mastercode and find out the lock status of your phone
eq. To remove restriction on lock 1 type following code:
#pw+(master code)+1#
If you just want to check your phone use 10 random numbers Eg. 1234567890 as the (master code)
eq. To check if phone if restricted on lock 1 type the following code:
#pw+1234567890+1#
Please NOTE that these codes could be used with care!
A user told me that it s only possible to type in about 3 different codes on each lock! Then something bad will happen ..therefore be careful!
---------------------------------------------------------
How can I check what locks have my phone closed?
There is 2 methods:
Use winlock to see the state of the locks, pressing Read Info.The Counter is the number of times that you have tried unlock your phone using an incorrect master code.
You can check it entering an imaginary mastercode on your phone but, it s not recommended because if you try enter a code 5 times your phone will not work anymore. By example, if you press at your phone #pw+1234567890+2# (note that # , p , w and + characters must be selected from * key) and your phone give you Code Error then your phone have lock 2 closed, if you get the message SIM Restriction Off your phone have lock 2 opened.
Look the table above to see how can check all locks:
Lock number Description Sequence to Check
1 Provider Lock #pw+1234567890+1#
2 Network-Lock #pw+1234567890+2#
3 Another Provider Lock #pw+1234567890+3#
4 SIM Card Lock #pw+1234567890+4#
---------------------------------------------------------
Unlock SP-Lock
Here is a way to Unlock your phone which is Service Provider locked, without to know SPLock code. With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIMlocked to one privider you can bypass the SP lock like this:
First of all, PIN CODE MUST BE ON, then press:
C
C and hold until it clears display
* and hold until start to blink
* and hold until start to blink
04***your pin>#
Each time you turn your phone OFF it resets the lock, so this need to be done each time you ll turn your phone ON
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
NOTE: On vesion 5.04 Nokia has removed this option !
update:
There s another Nokia service provider lock generator for DOS (somehere on the net) called 5161un.zip (for Nokia 51xx-61xx models) This program uses the #pw+(master code)+1# code to unlock the phone. With this software you need to have a access to the eeprom.. Sad
---------------------------------------------------------
Bypass the SP-lock
With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIM locked to one privider you can bypass the SP lock like this:
Insert sim card of diferent provider.
Turn on the phone and press the UP VOLUME key for 3 sec. then release it and the phone says PIN CODE ?
Press the "C" key.
Then Press * and wait until it desapear and apear again, then press * one more time and 04*PIN*PIN*PIN#
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
update:
On version 5.04 Nokia has removed this option !
---------------------------------------------------------
How to open lock 1 and 4?
You will need Winlock software and MBUS cable to do this. Winlock is a Nokia service program that you can use to open lock 1 and 4, really you are closing locks when you do that, but when you write ????? at MCC+MNC and MSIN text box, the phone don t understand it and consider that it s open.
That trick only works for lock 1 and 4, but not for lock 2 and 3. If you did not know your lock type, please read our miscellaneous tips page first. or read at above section in this page.
Install winlock 1.10
Connect your MBUS nokia data cable
Run Winlock
Push Read Phone, if you have Lock 2 or Lock 3 closed you can not open your phone, but you can try change Lock 2.
Select State Close in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ??????? and Push Close Locks.
Now you can use any operator card in your phone. If you get any error when you do that do the following steps:
Select State Automatic in Lock 1 and Lock 4 and change type to User in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
Select State Automatic in Lock 1 and Lock 4 and change type to Factory in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
If you continue getting errors you must turn off your phone and reset computer and try again.
---------------------------------------------------------
How to open lock 2?
When operators companies close lock2 you can only use the contract or prepaid card for this operator, but you can use another operator company prepaid card if you know what GID1 must write.
Install Winlock
Run Winlock
Configure Winlock. Select menu Winlock->Defaults and change GID byte count to 2.
Push Read Phone, and write down GID1 info that appear in lock 2.
Insert the prepaid card from a different operator company.
We must find out a the GID1 info adecuate for our new prepaid or contract card, take a look at our GID1 list and check if your operator and SIM card type is included, if not try to get a phone that have lock 2 closed and have the SIM card type that you want to use in your phone, and read GID1 info with winlock. You can try to write the most used GID1 codes like 0000,10FF,01FF, or FFFF, etc.
Change Lock 2 Type from User To Factory or from Factory to User.
Push Close Locks
Your phone will be reset every time you push Close Locks, if your card is not acepted the GID1 is not correct, repeat from step 4 until you find the correct GID1.
If you get error you must turn off your phone and reset computer and try again.
If you want your phone accept your original prepaid card write in GID1 the code you read at step 2 and close locks.
Exist a GID1 list?
In addition to the official way to open locks that Nokia service centers use with TDB4 or TDF-4(for WinTesla) security boxes, there is two secrets methods:
Opening the phone and adding a chip inside phone motherboard. But you will loose any warranty of your phone.
Using a special software with a MBUS Nokia cable. I don t have this software. Please don t bother me asking me about that. The only thing i know about that is that a friend is removing lock 2 using a special software. He don t make this for money, only for fun.
--------------------------------------------------------
Main Code #pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
update:
I get report that told me the code didn t works for Optimus Card
---------------------------------------------------------
Enhanced Full Rate Codec (EFR)
Enhanced Full Rate will give you much better sound quality when you enable it. The new Enhanced Full Rate CODEC adopted by GSM uses the ASELP (AlgebraicCode Excitation Linear Prediction) compression technology. This technology allows for much great voice quality in the same number of bits as the older Full Rate CODEC. The older technology was called LPC-RPE (Linear Prediction Coding with Regular Pulse Excitation). Both operate at 13 kilobits.(but you take up more space on the network, so they can charge you more)
*3370# and EFR will be activated after a reboot of the phone ( consumes more power )
#3370#
and EFR will be switched off after a reboot of the phone.
---------------------------------------------------------
Half Rate Codec (HR)
Half Rate will give you bad sound quality, which gives the service provider the opportunity to have more calls on the network; and you might get a lower charge from them. (Will give you 30% longer talk-time)
*4720# Half Rate coded will be activated after a reboot of the phone ( better standby time )
#4720# Half Rate coded will be de-activated after a reboot of the phone
---------------------------------------------------------
Unblocking Code
Unblock PIN1 : **05*PUK*newPIN1*newPIN1#@
UnBlock PIN2 : **052*PUK2*newPIN2*newPIN2#@
---------------------------------------------------------
Hiding your phone number
Dial 141 then the number you want to call eg. 141#######
This should stop your number been sent to the caller. (*)
(*) This only works on UK phones, if anybody has tried this and works, please let me know.
---------------------------------------------------------
Unlocking PIN2 for software version
V 05.07
20.11.98
NSE-1
If your SimCard is locked by your SP, you can check it and if it is, you will get the "wrong code" message on the display (for use 1234567890)
If your SimCard is locked by your SP, you can t unlock PIN2 !
---------------------------------------------------------
Blocking phone number at Cantel AT&T
If you have one of those cantel at&t phones if you press #0000# you can block your number
at no extra charge.
---------------------------------------------------------
New Menu on Emergency Calls *3001#12345#
Brings a new menu that gives you access to the emergency calls ( 911 Etc. ). It will give you FREE calls! (only the ones you put in the emergency!! )
This option will depend on your GSM operator
---------------------------------------------------------
Your number in your display
Goto menu 3-7 Call cost settings.
Turn ON the Call costs limit 3-7-1. PIN2 code Required.
Put in the limit with the phone number.
eg. my phone # is 019 2184697
Enter the limit as 2184697
Goto menu 3-7-2 Show costs in. PIN2 code Required.
Select Currency.
Enter Unit price : 1
Enter Currency name as 019 (per my phone # eg. above)
Now the phone number 019 2184697 will remains on the 4th row of the display.
Secondly, if you press the # key, it prompt which line to be used; Line 1 or 2.
---------------------------------------------------------
Free Call Tip
The tips needs Net Monitor enabled. Be aware that the trick will remove Netmonitor in some sw versions like v4.73 and v5.04.
Launch the Net Monitor in your Nokia 51xx / 61xx
Execute the test number 497
Free calling for about 90 sec should now have been activated.
---------------------------------------------------------
Nokia 5110 PIN-Out
Pin-Outs: Bottom view, keyboard up, counting from the left
V V 1 2 3 4 5 6 V
(o) | | [= = = = = =] | |
7 8 9 10 11 12
1 - VIN CHARGER INPUT VOLTAGE 8.4V 0.8A
2 - CHRG CTRL CHARGER CONTROL PWM 32Khz
3 - XMIC MIC INPUT 60mV - 1V
4 - SGND SIGNAL GROUND
5 - XEAR EAR OUTPUT 80mV - 1V
6 - MBUS 9600 B/S
7 - FBUS_RX 9.6 - 230.4 KB/S
8 - FBUS_TX 9.6 - 230.4 KB/S
9 - L_GND CHARGER / LOGIC GND
Nokia 61xx
__________
Firmware version
*#0000# or *#61x0#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
Nokia 81xx
_____________
Show IMEI code
* # 06 #
Software Version
* # 8110 #
This code shows you software version, date of manufacture and hardware number of your phone.
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Sim Clock information
To check if the Sim-Clock can be stopped type: *#746025625# (= *#sim0clock#)
Nokia 8810
____________
Firmware version
*#0000# or *#8810#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
____________
Firmware version
*#0000# or *#3110#
IMEI Code
*# 06 #
Restores Factory Settings
*#7780#
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Nokia 5110
_____________
IMEI Number *#06#
For checking the IMEI (International Mobile Equipment Identity).
---------------------------------------------------------
Security Code 12345
Default security code is 12345. If you forgot your security code, there s so many program on the net which allowed you to know the security code likes Security ID Generator, Nokia IMEI Changer, etc.
update:
Security ID Generator (SID.EXE) and IMEI Generator (NOKIAIMEI.EXE) doesn t works with Nokia 5110
Resetting Security Code
If you accidentally lock the phone or forgot the security code, the best thing to do is check it with your local Nokia dealer. For advanced user, you can use WinTesla, PCLocals or LogoManager program to read the security code or resetting the code (You will need an FBUS/MBUS (or compatible) cable to do this.
---------------------------------------------------------
Software Version *#0000#
For checking the phones software (SW) - called firmware revision information.
e.q : Version V. 4.51 (26-03-98) will display
V 04.51
26-03-98
NSE-1
first line:
The Software Version (my guess is that this software has been used in previously Nokia-phones, what do you say?!).
second line:
The Date of the SW release.
third line:
NHE-8 has something to do with the type of phone you are dealing with. Is it GSM 900 (standard), GSM 1800 (DCS1800) or GSM 1900 (PCS1900)?
Nokia 2110, 3110, 8110(i) are all NHE types. The only thing that vary is the code after NHE- ("8").
NHE = GSM 900, NHK =GSM 1800 - The number in the end = the model (2110i = 4 etc.)
The 5110 and 6110 is called NSE-1 and NSE-3...this may be because it supports EFR (?)
update:
Newest Software Version was V5.22 (xx-xx-99)
V 05.22
01-07-99
NSE-1
If your software version is V4.00, upgrade your software version to latest version. V4.00 contains bugs that sometimes will show message,
"SIM Card Not Ready" even the card is already inside the phone.
---------------------------------------------------------
Software Update
The only thing to do (for you and me) is for us to go to the nearest Nokia dealer and make him do it for you. Just remember that it is supposed to be free (a receipt is required) so don t let him tell you anything else!
---------------------------------------------------------
SIM clock *#746025625# [*#sim0clock#]
to check if the Sim-Clock can be Stopped. This option is depen on your service provider network. (Sim-clock-stop is a kind of standby mode which will save battery time)
update:
This code doesn t work on phone with software version 4.59.
---------------------------------------------------------
Waranty Code *#92702689# [*#war0anty#]
Menu:
Displays Serial Number.
Displays the Month and Year of Manufacture (0698)
Displays (if there) the date where the phone was purchased (MMYY) you can here set the Purchasing Date
(Warning: You can only do this once - so be careful what you write)
Displays the date of the last repairment - if found (0000)
The next screen has Transfer User Data? (the same option as the 8110)
To exit turn the phone off and then back on.
---------------------------------------------------------
SP Lock The Service provider (SP) lock
Is used to lock the cell phone to the SP s SIM card. Once the cell phone is locked to a specific operator, if one inserts a SIM card from a different operator the phone will refuse to accept it!
The cell phone will however accept another SIM card from the same operator.
All Nokia phones (2110 and newer) have four different SIM locks which can be used to lock the phone for up to 4 different providers. But most phones with restriction only have one lock activated. ( lock 1)
The main code used in Nokia phones is:
#pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
(I can NOT give you the master code SO DON T ASK ME FOR IT! )
Please click here to learn more about how to obtain mastercode and find out the lock status of your phone
eq. To remove restriction on lock 1 type following code:
#pw+(master code)+1#
If you just want to check your phone use 10 random numbers Eg. 1234567890 as the (master code)
eq. To check if phone if restricted on lock 1 type the following code:
#pw+1234567890+1#
Please NOTE that these codes could be used with care!
A user told me that it s only possible to type in about 3 different codes on each lock! Then something bad will happen ..therefore be careful!
---------------------------------------------------------
How can I check what locks have my phone closed?
There is 2 methods:
Use winlock to see the state of the locks, pressing Read Info.The Counter is the number of times that you have tried unlock your phone using an incorrect master code.
You can check it entering an imaginary mastercode on your phone but, it s not recommended because if you try enter a code 5 times your phone will not work anymore. By example, if you press at your phone #pw+1234567890+2# (note that # , p , w and + characters must be selected from * key) and your phone give you Code Error then your phone have lock 2 closed, if you get the message SIM Restriction Off your phone have lock 2 opened.
Look the table above to see how can check all locks:
Lock number Description Sequence to Check
1 Provider Lock #pw+1234567890+1#
2 Network-Lock #pw+1234567890+2#
3 Another Provider Lock #pw+1234567890+3#
4 SIM Card Lock #pw+1234567890+4#
---------------------------------------------------------
Unlock SP-Lock
Here is a way to Unlock your phone which is Service Provider locked, without to know SPLock code. With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIMlocked to one privider you can bypass the SP lock like this:
First of all, PIN CODE MUST BE ON, then press:
C
C and hold until it clears display
* and hold until start to blink
* and hold until start to blink
04***your pin>#
Each time you turn your phone OFF it resets the lock, so this need to be done each time you ll turn your phone ON
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
NOTE: On vesion 5.04 Nokia has removed this option !
update:
There s another Nokia service provider lock generator for DOS (somehere on the net) called 5161un.zip (for Nokia 51xx-61xx models) This program uses the #pw+(master code)+1# code to unlock the phone. With this software you need to have a access to the eeprom.. Sad
---------------------------------------------------------
Bypass the SP-lock
With a Nokia 16xx/21xx/31xx/51xx/81xx that are SIM locked to one privider you can bypass the SP lock like this:
Insert sim card of diferent provider.
Turn on the phone and press the UP VOLUME key for 3 sec. then release it and the phone says PIN CODE ?
Press the "C" key.
Then Press * and wait until it desapear and apear again, then press * one more time and 04*PIN*PIN*PIN#
The phone now says: PIN CODE CHANGED (or ACCEPTED)
and the SIM card is accepted until you restart the phone again.
update:
On version 5.04 Nokia has removed this option !
---------------------------------------------------------
How to open lock 1 and 4?
You will need Winlock software and MBUS cable to do this. Winlock is a Nokia service program that you can use to open lock 1 and 4, really you are closing locks when you do that, but when you write ????? at MCC+MNC and MSIN text box, the phone don t understand it and consider that it s open.
That trick only works for lock 1 and 4, but not for lock 2 and 3. If you did not know your lock type, please read our miscellaneous tips page first. or read at above section in this page.
Install winlock 1.10
Connect your MBUS nokia data cable
Run Winlock
Push Read Phone, if you have Lock 2 or Lock 3 closed you can not open your phone, but you can try change Lock 2.
Select State Close in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ??????? and Push Close Locks.
Now you can use any operator card in your phone. If you get any error when you do that do the following steps:
Select State Automatic in Lock 1 and Lock 4 and change type to User in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
Select State Automatic in Lock 1 and Lock 4 and change type to Factory in Lock 1 and Lock 4, fill out MCC+MNC and MSIN text boxes with ?????????? and Push Close Locks.
If you continue getting errors you must turn off your phone and reset computer and try again.
---------------------------------------------------------
How to open lock 2?
When operators companies close lock2 you can only use the contract or prepaid card for this operator, but you can use another operator company prepaid card if you know what GID1 must write.
Install Winlock
Run Winlock
Configure Winlock. Select menu Winlock->Defaults and change GID byte count to 2.
Push Read Phone, and write down GID1 info that appear in lock 2.
Insert the prepaid card from a different operator company.
We must find out a the GID1 info adecuate for our new prepaid or contract card, take a look at our GID1 list and check if your operator and SIM card type is included, if not try to get a phone that have lock 2 closed and have the SIM card type that you want to use in your phone, and read GID1 info with winlock. You can try to write the most used GID1 codes like 0000,10FF,01FF, or FFFF, etc.
Change Lock 2 Type from User To Factory or from Factory to User.
Push Close Locks
Your phone will be reset every time you push Close Locks, if your card is not acepted the GID1 is not correct, repeat from step 4 until you find the correct GID1.
If you get error you must turn off your phone and reset computer and try again.
If you want your phone accept your original prepaid card write in GID1 the code you read at step 2 and close locks.
Exist a GID1 list?
In addition to the official way to open locks that Nokia service centers use with TDB4 or TDF-4(for WinTesla) security boxes, there is two secrets methods:
Opening the phone and adding a chip inside phone motherboard. But you will loose any warranty of your phone.
Using a special software with a MBUS Nokia cable. I don t have this software. Please don t bother me asking me about that. The only thing i know about that is that a friend is removing lock 2 using a special software. He don t make this for money, only for fun.
--------------------------------------------------------
Main Code #pw+(master code)+Y#
This code is able to check, activate or remove Sim card restriction (SP-lock).
Use the * key to get the p, + and w chars.
Y has to be 1,2,3 or 4 - depending of what lock you what to deal with.
#pw+1234567890+1# for Provider-Lock status
#pw+1234567890+2# for Network-Lock status
#pw+1234567890+3# for Provider(???)-Lock status
#pw+1234567890+4# for SimCard-Lock status
(master code) is a 10 digit code, based on the phones IMEI number.
update:
I get report that told me the code didn t works for Optimus Card
---------------------------------------------------------
Enhanced Full Rate Codec (EFR)
Enhanced Full Rate will give you much better sound quality when you enable it. The new Enhanced Full Rate CODEC adopted by GSM uses the ASELP (AlgebraicCode Excitation Linear Prediction) compression technology. This technology allows for much great voice quality in the same number of bits as the older Full Rate CODEC. The older technology was called LPC-RPE (Linear Prediction Coding with Regular Pulse Excitation). Both operate at 13 kilobits.(but you take up more space on the network, so they can charge you more)
*3370# and EFR will be activated after a reboot of the phone ( consumes more power )
#3370#
and EFR will be switched off after a reboot of the phone.
---------------------------------------------------------
Half Rate Codec (HR)
Half Rate will give you bad sound quality, which gives the service provider the opportunity to have more calls on the network; and you might get a lower charge from them. (Will give you 30% longer talk-time)
*4720# Half Rate coded will be activated after a reboot of the phone ( better standby time )
#4720# Half Rate coded will be de-activated after a reboot of the phone
---------------------------------------------------------
Unblocking Code
Unblock PIN1 : **05*PUK*newPIN1*newPIN1#@
UnBlock PIN2 : **052*PUK2*newPIN2*newPIN2#@
---------------------------------------------------------
Hiding your phone number
Dial 141 then the number you want to call eg. 141#######
This should stop your number been sent to the caller. (*)
(*) This only works on UK phones, if anybody has tried this and works, please let me know.
---------------------------------------------------------
Unlocking PIN2 for software version
V 05.07
20.11.98
NSE-1
If your SimCard is locked by your SP, you can check it and if it is, you will get the "wrong code" message on the display (for use 1234567890)
If your SimCard is locked by your SP, you can t unlock PIN2 !
---------------------------------------------------------
Blocking phone number at Cantel AT&T
If you have one of those cantel at&t phones if you press #0000# you can block your number
at no extra charge.
---------------------------------------------------------
New Menu on Emergency Calls *3001#12345#
Brings a new menu that gives you access to the emergency calls ( 911 Etc. ). It will give you FREE calls! (only the ones you put in the emergency!! )
This option will depend on your GSM operator
---------------------------------------------------------
Your number in your display
Goto menu 3-7 Call cost settings.
Turn ON the Call costs limit 3-7-1. PIN2 code Required.
Put in the limit with the phone number.
eg. my phone # is 019 2184697
Enter the limit as 2184697
Goto menu 3-7-2 Show costs in. PIN2 code Required.
Select Currency.
Enter Unit price : 1
Enter Currency name as 019 (per my phone # eg. above)
Now the phone number 019 2184697 will remains on the 4th row of the display.
Secondly, if you press the # key, it prompt which line to be used; Line 1 or 2.
---------------------------------------------------------
Free Call Tip
The tips needs Net Monitor enabled. Be aware that the trick will remove Netmonitor in some sw versions like v4.73 and v5.04.
Launch the Net Monitor in your Nokia 51xx / 61xx
Execute the test number 497
Free calling for about 90 sec should now have been activated.
---------------------------------------------------------
Nokia 5110 PIN-Out
Pin-Outs: Bottom view, keyboard up, counting from the left
V V 1 2 3 4 5 6 V
(o) | | [= = = = = =] | |
7 8 9 10 11 12
1 - VIN CHARGER INPUT VOLTAGE 8.4V 0.8A
2 - CHRG CTRL CHARGER CONTROL PWM 32Khz
3 - XMIC MIC INPUT 60mV - 1V
4 - SGND SIGNAL GROUND
5 - XEAR EAR OUTPUT 80mV - 1V
6 - MBUS 9600 B/S
7 - FBUS_RX 9.6 - 230.4 KB/S
8 - FBUS_TX 9.6 - 230.4 KB/S
9 - L_GND CHARGER / LOGIC GND
Nokia 61xx
__________
Firmware version
*#0000# or *#61x0#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
Nokia 81xx
_____________
Show IMEI code
* # 06 #
Software Version
* # 8110 #
This code shows you software version, date of manufacture and hardware number of your phone.
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Sim Clock information
To check if the Sim-Clock can be stopped type: *#746025625# (= *#sim0clock#)
Nokia 8810
____________
Firmware version
*#0000# or *#8810#
IMEI Code
* # 06 #
Warranty Codes
*#92702689# (= *#war0anty#)
Just scroll down through the information. If entering the above code requires a
further warranty code try entering the following:
6232 (OK) : Month and year of manufacture
7332 (OK) : Last repair date
7832 (OK) : Purchase date (if previously set)
9268 (OK) : Serial number
37832 (OK) : Set purchase date (this can only be done once)
87267 (OK) : Confirm transfer
Enhanced Full Rate (EFR) and Half Rate Mode (HFR)
*3370# to activate Enhanced Full Rate - Makes calls sound better, but
decreases the battery life by about 5%.(I recommend this one)
#3370# to deactivate Enhanced Full Rate
*4720# to activate Half Rate Mode - Drops call quality, but increases battery
life by about 30%.
#4720# to deactivate Half Rate Mode
Subscribe to:
Posts (Atom)
